Using DNSSEC (Linux)
Watch the video tutorial
DNSSEC is the extension of the DNS protocol that allows signing of DNS data in order to secure the domain name resolving process. For general information about DNSSEC and its usage, visit ICANN website and https://tools.ietf.org/html/rfc6781.
Plesk enables you to protect the DNS data of hosted domains with DNSSEC. You can do the following:
- Configure the settings used for key generation and rollover.
- Sign and unsign domain zones according to the DNSSEC specifications.
- Receive notifications.
- View and copy DS resource records.
- View and copy DNSKEY resource record sets.
Requirements
- Plesk for Linux with the Bind DNS server, starting from Bind 9.9.
- DNSSEC is a paid extension. It is included for free in Plesk Web Host and Plesk Web Pro editions.
- DNSSEC is available on Debian 8, Debian 9, Ubuntu 14.04, Ubuntu 16.04, Ubuntu 18.04, CentOS 7, RedHat Enterprise Linux 7, CloudLinux 7, Virtuozzo Linux 7.
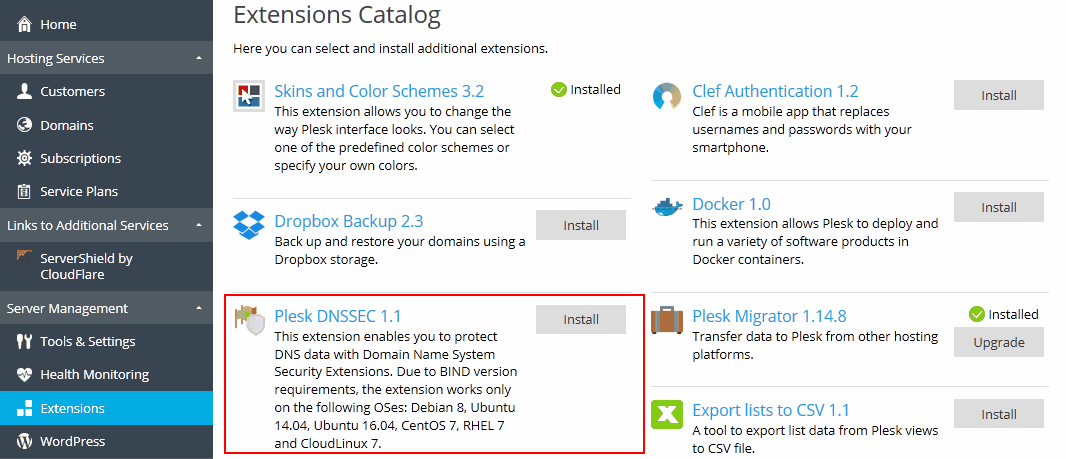
Enabling DNSSEC Support
To enable the support for DNSSEC, install the Plesk DNSSEC extension (Extensions > Extensions Catalog).
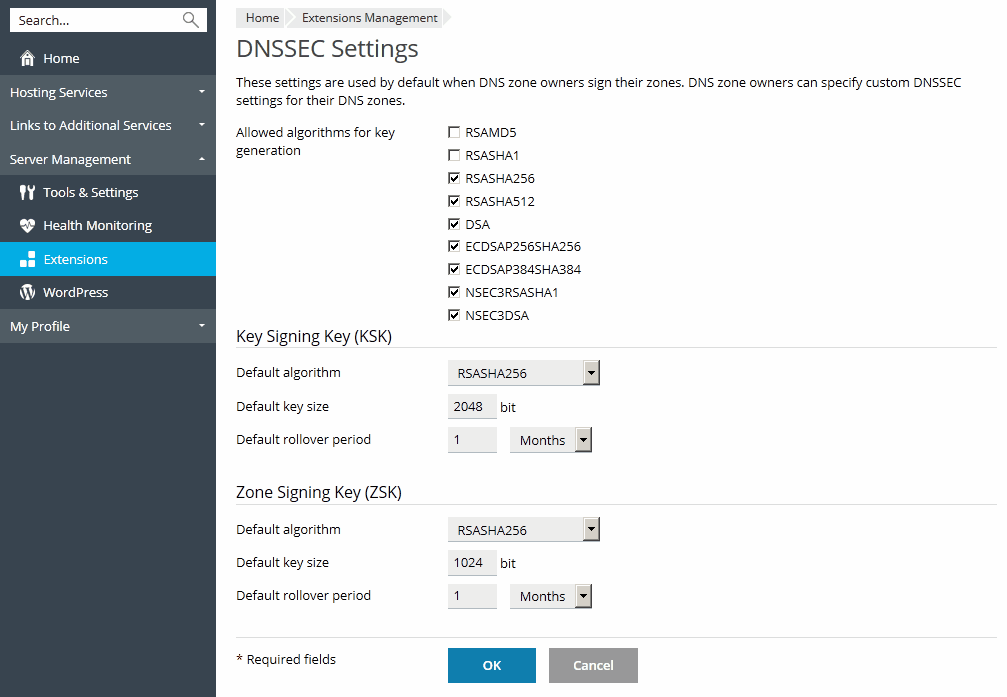
Configuring Default DNSSEC Settings
The default DNSSEC settings are located in Tools & Settings > Extensions > DNSSEC. You can change the default policy for generating Key Singing Key (KSK) and Zone Signing Key (ZSK) pairs.
The recommended policy for KSK and ZSK:
-
Use a long key and a long rollover period for the KSK (Key Signing Key).
Every time the Key Signing Key is updated, the zone owner needs to update the DS records in the parent domain zone. The recommended policy helps to update DS records in the parent zone as seldom as possible without decreasing security.
-
Use a shorter key and a shorter rollover period for the ZSK (Zone Signing Key).
The Zone Signing Key is updated automatically. The recommended policy helps to save system resources without decreasing security.
When hosting customers sign their zones, they can use the default values or specify different values. For details, see Using DNSSEC on Domains.
Protecting DNS Zones with DNSSEC
To use DNSSEC, domain owners must sign their DNS zones. For details, see Using DNSSEC on Domains.
How Key Rollover Works in Plesk
In order to prevent DNS outage for a domain, Plesk uses more than one key as the KSK and more than one key as the ZSK. A previously generated key exists in parallel with a new key for some time, to allow all the changes in a DNS zone to take effect. Obsolete keys are removed automatically.
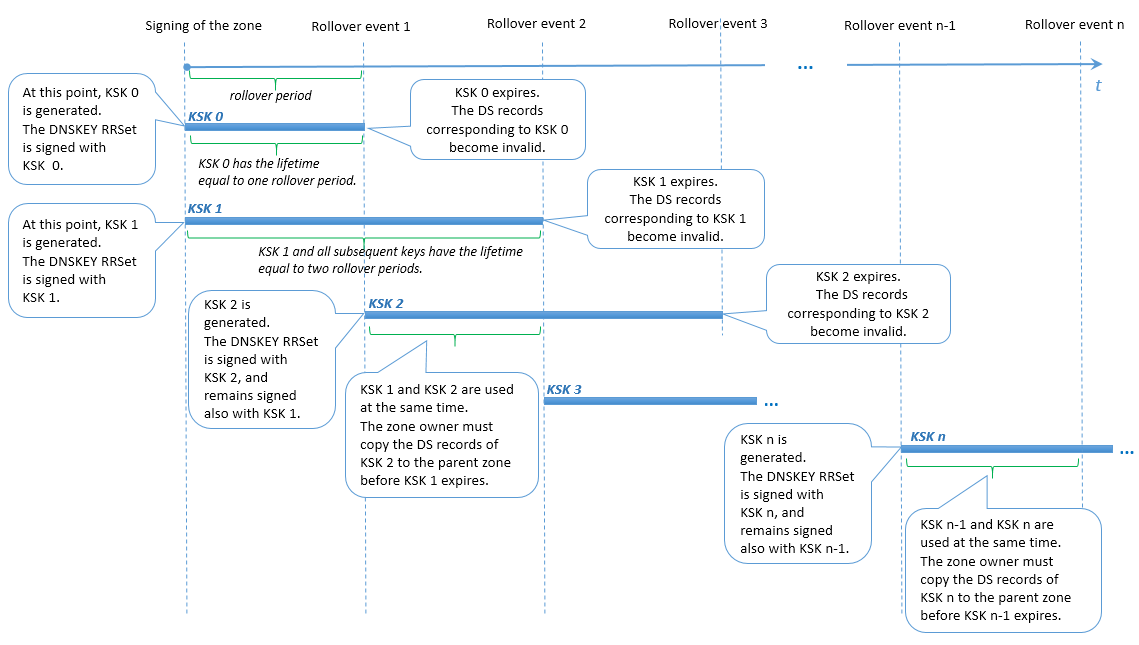
KSK rollover
Plesk uses a modification of the Double-RRset method for rolling over Key Signing Keys. The difference is that Plesk has two Key Signing Keys during each rollover period. This measure allows enough time for the domain zone owner to update the corresponding DS records in the parent zone (for example, the time period between rollover events 1 and 2 in the scheme below).
User actions at KSK rollover
The domain zone owner is notified about the rollover and about the need to update the DS records in the parent zone. The DS records become obsolete when the oldest KSK expires and the newest KSK is generated (for example, at rollover event 2 in the scheme below). If the domain zone owner did not update the DS records in the parent zone, then at the end of one rollover period after the notification the domain stops resolving.
Note: At the moment, the text of the domain zone owner notification cannot be customized.
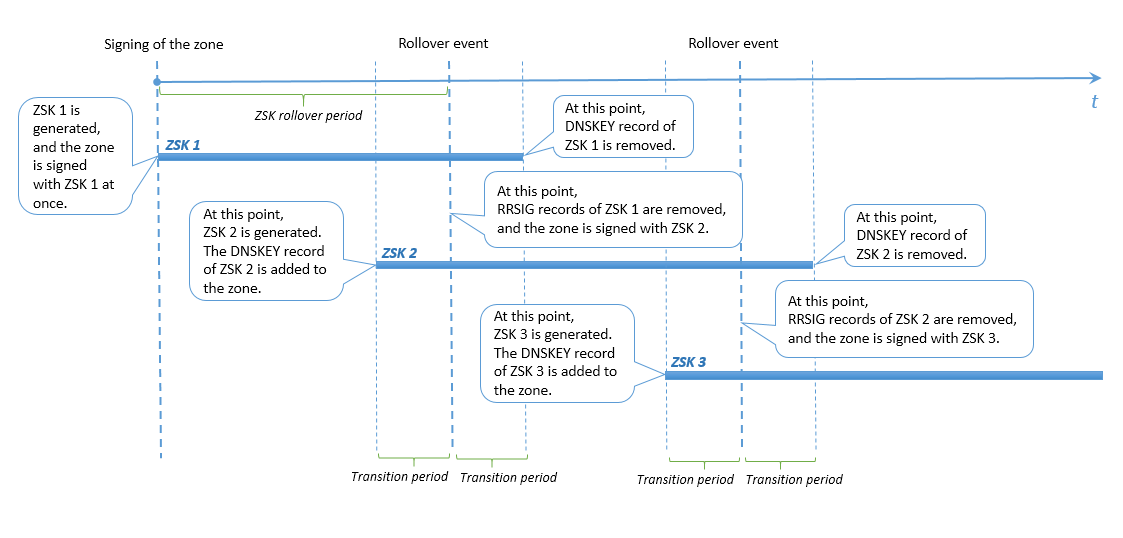
ZSK rollover
To allow enough time for slave and caching DNS servers to sync with the master DNS server, Plesk does the following:
- Adds a new key to the zone at a specific time before the rollover event.
- Removes the previous key at the same specific time after the rollover event.
This certain time before or after a ZSK rollover is called a transition period in Plesk. The transition period is either 30 days or the sum of a zone’s SOA TTL and SOA Expire values (if that sum is over 30 days). However, the transition period cannot be longer than half the ZSK rollover period, otherwise the rollover functionality would be disrupted and the zone signatures would become invalid.
Therefore, to make sure that ZSK rollover is performed correctly, Plesk sets limits on the following values:
- The zone’s SOA TTL and SOA Expire values. Their sum cannot be longer than a certain calculated value.
- The ZSK rollover period. It cannot be shorter than a certain calculated value.
User actions at ZSK rollover
No actions are required of the domain’s DNS zone owner when Zone Signing Keys are rolled over.