(Plesk for Linux) Protection Against Brute Force Attacks (Fail2Ban)
概要: IP address banning (or Fail2Ban) is a tool protecting your server and the hosted websites from brute-force attacks.
In this topic, you will learn how to:
- Enable and configure Fail2Ban to ensure optimal protection with minimal effort.
- Manually block connections from certain IP addresses, and how to manually unblock connections from banned IP addresses.
- Ensure that connections from certain IP addresses are never blocked by Fail2Ban.
- Create, configure, remove, activate, and deactivate Fail2Ban jails, and how to add filters used by Fail2Ban jails.
概要
Fail2Ban protects your server by scanning the log files of various Plesk services. It searches for entries signifying authentication failures, known attacks, and other suspicious entries, coming from specific IP addresses. When the number of such log entries associated with a specific IP address reaches a predefined value, Fail2Ban either sends a notification email or “bans” that IP address (blocks further access from that IP address by adding a corresponding rule to the server’s firewall configuration) for a predefined length of time (“ban period”).
For example, with the default Fail2Ban configuration in effect, once the fifth failed attempt to log in to Plesk from the IP address 198.51.100.1 is logged within a period of ten minutes, the following rule is added to the firewall configuration:
Chain f2b-plesk-login (1 references)
target prot opt source destination
REJECT all -- 198.51.100.1 anywhere reject-with icmp-port-unreachable
When the ten minute ban period is over, the IP address is automatically unbanned, and the corresponding firewall rule is removed.
The Fail2Ban logic is governed by the use of “jails”. A jail is a combination of a “filter”, a set of one or more regular expressions that is used to detect violations, and an “action”, a directive governing what is to be done once a sufficient number of violations from a specific IP address have been detected.
A single jail usually corresponds to a single service running on the server, such as the web server or the SSH server. Plesk comes with a number of preconfigured jails out of the box, covering most Plesk services. You can also add custom jails manually.
Caveats and Limitations
When using Fail2Ban in Plesk, keep in mind the following limitations:
- Fail2Ban relies solely on IP addresses, and does not perform hostname lookups unless configured to do so.
- Fail2Ban must use its strictest settings to provide any protection from distributed brute-force attacks, since it identifies intruders by their IP address. Such settings may cause trouble to legitimate users in case of false positives.
Enabling Fail2Ban
On Plesk servers installed with the “Recommended” preset, Fail2Ban is enabled by default, and all default jails are activated. If Fail2Ban is not enabled on your server (for example, because it is not installed), you need to install and enable it, and also to activate the default jails before you can take advantage of the protection it offers.
To install and enable Fail2Ban:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”). If IP Address Banning (Fail2Ban) is missing, you need to install the “Fail2Ban” component first.
- Select the “Enable intrusion detection” checkbox, and then click Apply.
- Go to the “Jails” tab, select all jails marked as “Inactive”, and then click Switch On.
Fail2Ban is now working with the default settings. To disable Fail2Ban, clear the “Enable intrusion detection” checkbox found on the “Settings” tab, and then click OK.
Configuring Fail2Ban
The default Fail2Ban settings are optimal in most scenarios. However, you may wish to change them to make Fail2Ban more strict or more lenient, depending on your needs.
若要更改 Fail2Ban 设置,请如下操作:
-
Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”).
-
Go to the “Settings” tab.
-
(Optional) Change the “IP address ban period” value to make the period an IP address is banned for longer or shorter. Setting it to “-1” will result in all bans being permanent.
A longer ban period will keep an attacker out for longer, but will also keep a legitimate user out for longer in case of a false positive. A permanent ban will stop all further attacks from an IP address, but will also permanently lock a legitimate user out in case of a false positive. You can manually unban any IP address at any time.
-
(Optional) Change the “Time interval for detection of subsequent attacks” value to make the period any individual log entry indicating an authentication failure or a potential attack remains “alive” longer or shorter.
The longer the period, the greater the chance of detecting and blocking attacks coming at intervals, as well as the chance of false positives, as authentication failures of legitimate users are also kept track of for longer.
-
(Optional) Change the “Number of failures before the IP address is banned” value to set the number of authentication failures or potential attacks coming from a single IP address necessary for it to be banned.
The smaller the value, the less authentication failures or potential attacks must be detected for a ban to occur. This increases the security at the expense of also increasing the likelihood of false positives. Setting the value of this parameter to “1” will result in a ban every time an authentication failure or a potential attack is detected, providing maximum protection, but also maximizing the chance of false positives.
-
点击 确定 。
The configured settings will now come into effect. Note that these settings can also be changed for individual jails, and the settings of an individual jail take precedence over those configured on the “Settings” tab.
Manually Banning and Unbanning IP Addresses
You can see what IP addresses are currently banned by Fail2Ban. You can also manually issue a ban to an IP address, or unban an IP address that has been banned.
To see the list of currently banned IP addresses:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”).
- Go to the “Banned IP Addresses” tab.
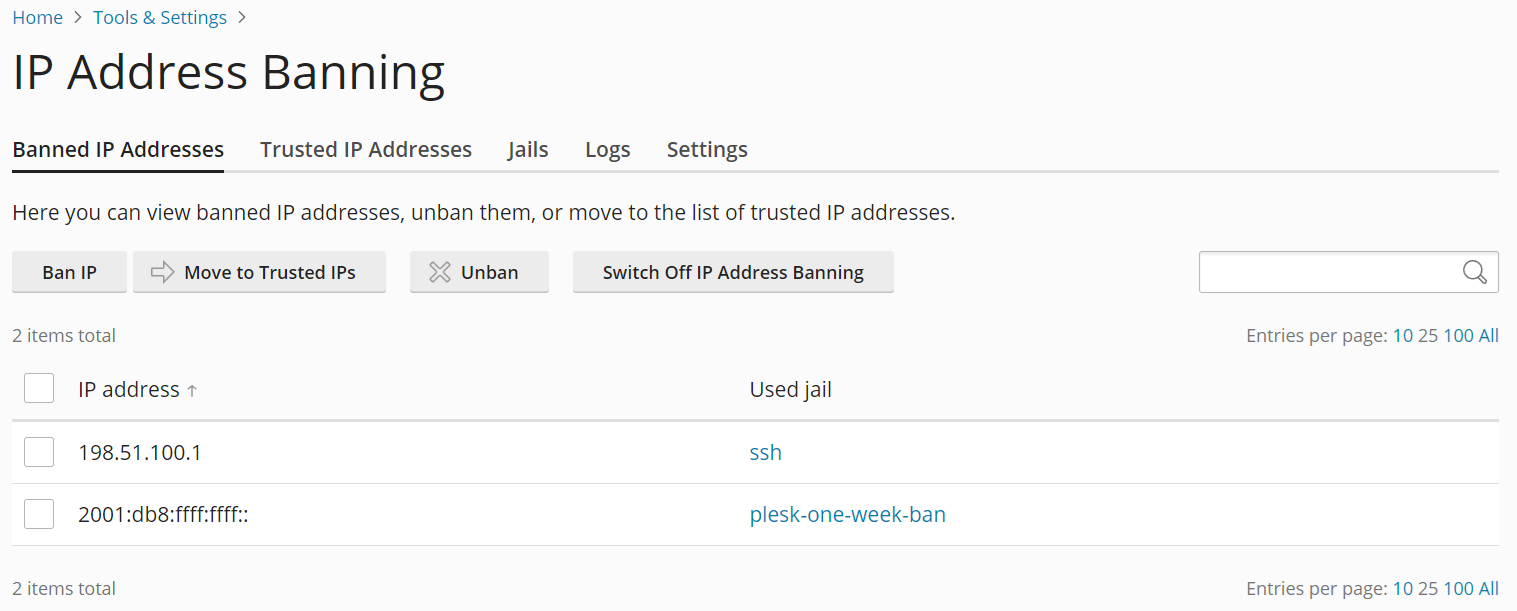
On this tab, you can see all the IP addresses that are currently banned by Fail2Ban, together with the names of the jails responsible for the ban.
To manually ban one or more IP addresses:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”).
- Go to the “Banned IP Addresses” tab, and then click Ban IP.
- Specify the IP address or the CIDR subnet mask you want to ban under “IP address”.
- Select the desired ban length under “Ban the IP address”, and then click OK.
The specified IP address or addresses are now banned. You can see them on the “Banned IP Addresses” tab.
You can manually unban an IP address at any time, whether it was banned automatically or manually.
To manually unban one or more IP addresses:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”).
- Go to the “Banned IP Addresses” tab.
- Select the IP address or addresses you want to unban from the list of the currently banned IP addresses, and then click Unban.
The selected IP address or addresses are no longer banned.
Preventing Specific IP Addresses or Hostnames from Being Banned
You can prevent specific IP addresses, subnets, or hostnames from ever being banned by Fail2Ban. This can be used, for example, to ensure that you are never locked out of the server by Fail2Ban.
Preventing an IP address, subnet, or hostname from being banned:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”).
- Go to the “Trusted IP Addresses” tab, and then click Add Trusted IP.
- Specify the IP address, the CIDR subnet mask, or the hostname you want to never be banned under “IP address”.
- (Optional) Add a message stating the reason for adding the IP address, the CIDR Subnet Mask, or the hostname to the list under “Description”. This message will be shown on the “Trusted IP Addresses” tab.
- 点击 确定 。
The specified IP address, CIDR subnet mask, or hostname will not be banned by Fail2Ban even if they trigger one or more active jails. You can see the list of IP addresses, CIDR subnet masks, and hostnames that cannot be banned by Fail2Ban on the “Trusted IP Addresses” tab.
Viewing and Downloading the Fail2Ban Log File
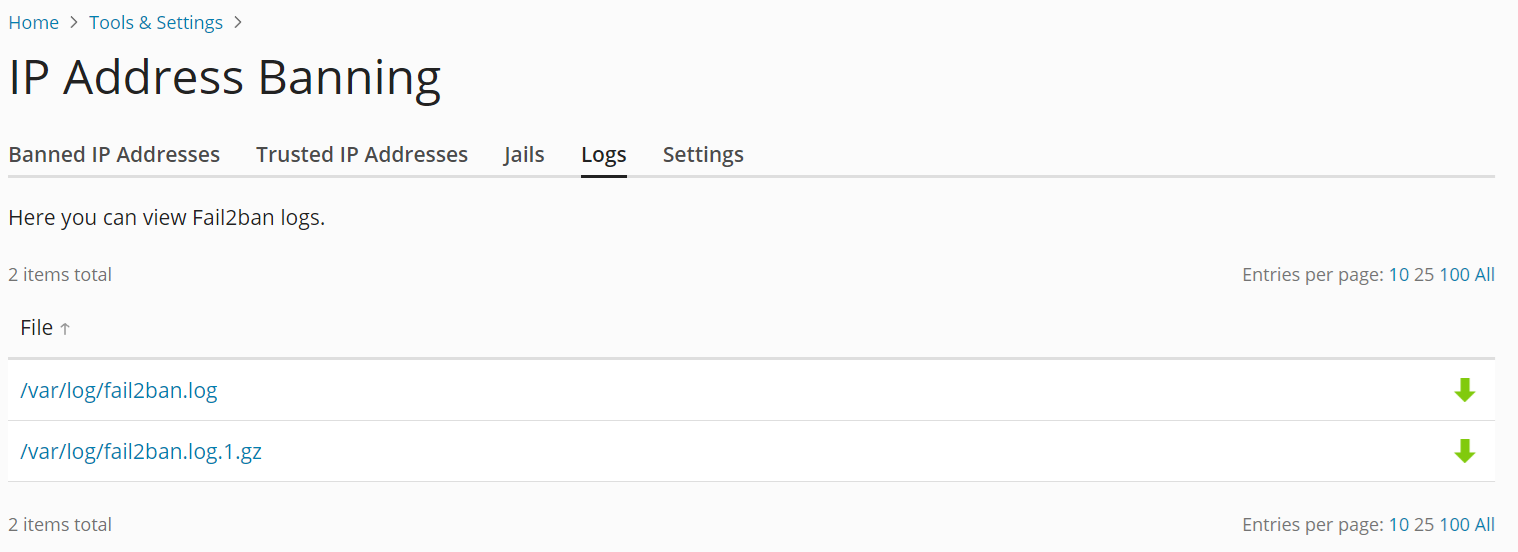
Fail2Ban writes the information about IP addresses being banned and unbanned, as well as other information (such as jails being created or activated) to a log file. You can view Fail2Ban logs from the Plesk graphical interface, and also download them to your computer.
To view or download the Fail2Ban log file:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”).
- Go to the “Logs” tab, and then click a log file to view it.
- (Optional) Click the
icon next to a log file to download it to your computer.
Activating and Deactivating Jails
For Fail2Ban to protect a specific Plesk service, the corresponding jail must exist and be activated. Plesk comes with a number of jails covering most Plesk services out of the box. Also, additional custom jails may be added manually.
若要激活 jail,请如下操作:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”), and then go to the “Jails” tab.
- Select one or more jails, and then click the Switch On button. This button is available only when the Fail2Ban service is running (the “Enable intrusion detection” checkbox is selected on the “Settings” tab).
The selected jail(s) are now active. Fail2Ban will now be banning IP addresses that trigger the activated jails.
注解: When activating several jails at once, if one of the jails fails to be activated, none of the selected jails will be activated. In this case, activate the jails one by one.
若要停用 jail,请如下操作:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”), and then go to the “Jails” tab.
- Select one or more jails, and then click the Switch Off button.
The selected jail(s) are now inactive. Fail2Ban will no longer be banning IP addresses that would trigger the deactivated jails. Also, all IP addresses that were banned by the deactivated jails are now unbanned.
注解: The plesk-one-week-ban and the plesk-permanent-ban jails cannot be deactivated.
Adding and Removing Custom Jails
If none of the default Plesk jails cover a specific service or protect against a specific attack, you can rectify that issue by adding a custom jail.
注解: When adding a custom jail, you will probably need to add a new filter first.
To add a custom jail:
-
Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”), and then go to the “Jails” tab.
-
单击 添加 Jail 。
-
Give the jail a name by entering it under “Name”.
-
Select the filter the jail will use from the “Filter” menu. You can use one of the default filters, or one you added manually.
-
Add one or more jail actions to be taked whenever the jail is triggered by either entering them in free-form, or selecting one of the four preconfigured actions from the “Action” menu, and then clicking Add. The following preconfigured actions are available:
-
iptables bans the IP address that has triggered the jail on a single port. Specify the parameters of the firewall rule to be added, for example:
iptables[chain="INPUT", name="ssh", port="22", protocol="tcp"] -
iptables-multiport bans the IP address that has triggered the jail on multiple ports. Specify the parameters of the firewall rule to be added, for example:
iptables-multiport[chain="INPUT", name="apache", port="80,443", protocol="tcp"] -
iptables-allports bans an attacker on all ports. There is no need to specify any parameters other than the name, for example:
iptables-allports[name=recidive] -
sendmail sends an email notification to the specified email address. Specify the destination email address, for example:
sendmail[mailcmd='/usr/sbin/sendmail -f "fail2ban@example.com" "mail@example.com"', dest="root", sender="fail2ban", sendername="Fail2Ban", name="default"]In this example, an email from “fail2ban@example.com” will be sent to “mail@example.com”.
-
-
Specify one or more log files Fail2ban will be scanning using the selected filter under “Log path”.
-
Specify the length of the ban in seconds under “IP address ban period”.
-
Specify the number of failed login attempts necessary for a ban to be issued “The maximum number of failed login attempts”.
-
点击 确定 。
The jail now exists and is active. You can find it on the “Jails” tab.
To remove one or more custom jails:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”), and then go to the “Jails” tab.
- Select one or more custom jails, click Remove, and then click Yes, remove.
The selected jail(s) are now removed and will no longer be shown on the “Jails” tab. Also, all IP addresses that were banned by the removed jails are now unbanned.
注解: The default Plesk jails cannot be removed.
Editing Jails
You can edit the properties of both default and custom jails.
注解: Changing a jail’s “IP address ban period” or “The maximum number of failed login attempts” values will result in those values overriding the default ones specified on the “Settings” tab.
要更改现有 jail 设置,请执行下列步骤:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”), and then go to the “Jails” tab.
- Click the jail’s name, and then click Change Settings.
- Edit the jail’s settings, and then click OK.
The jail’s new settings are now in effect.
Adding and Removing Filters
A filter is a combination of regular expressions that is used to scan log files for entries matching specific patterns associated with attacks or authentication failures. Generally, you need at least one filter for each service you want Fail2Ban to protect, as a filter that is meant to find irregularities in Apache log files is unsuitable for use with Postfix, and vice versa.
注解: A filter must have the correct syntax to work properly. Learn how to develop Fail2Ban filters.
To add a filter:
- 登录到 Plesk。
- Go to Tools & Settings > IP Address Banning (Fail2Ban) (under “Security”), and then go to the “Jails” tab.
- Click Manage Filters, and then click Add Filter.
- Specify the filter name and the regular expression used to match the lines of log files.
Default Plesk Fail2Ban Jails
Plesk comes with a number of preconfigured jails out of the box. They cover all hosting services (web server, mail server, FTP server, and so on). The following preconfigured jails are available:
| Name | Function |
|---|---|
| plesk-apache | Scans for Apache authentication failures. |
| plesk-apache-badbot | Scans Apache access logs for email grabbers and vulnerability scanners. |
| plesk-dovecot | Scans for Dovecot IMAP, POP3, and Sieve authentication failures. |
| plesk-modsecurity | Bans the IP addresses detected as harmful by the ModSecurity Web Application Firewall. The jail can only be activated if ModSecurity is running, and will ban attackers even if ModSecurity is operating in the “Detection only” mode. |
| plesk-one-week-ban | Used to block IP addresses that have been manually banned for one week. This jail cannot be deactivated or edited. |
| plesk-panel | Scans for Plesk authentication failures. |
| plesk-permanent-ban | Used to block IP addresses that have been manually permanently banned. This jail cannot be deactivated or edited. |
| plesk-postfix | Scans for Postfix SMTP and SASL authentication failures. |
| plesk-proftpd | Scans for ProFTPD authentication failures. |
| plesk-roundcube | Scans for Roundcube webmail authentication failures. |
| plesk-wordpress | Scans for WordPress authentication failures. |
| recidive | Scans the Fail2Ban log for bans issued by other jails. Blocks IP addresses that are repeatedly banned by other jails within a short period of time from accessing Plesk or any of the Plesk services for one week. |
| ssh | Scans for SSH authentication failures. |
Default Plesk Fail2Ban Filters
Plesk comes with a number of preconfigured filters out of the box. They cover all hosting services (web server, mail server, FTP server, and so on). These filters are used in the default Plesk jails, and can also be used with custom jails. The following preconfigured filters are available:
| Name | Function |
|---|---|
| apache-auth | Scans for Apache authentication failures. |
| apache-badbots | Scans for spam bots and bad web crawlers. |
| plesk-courierlogin | Scans for Courier IMAP and POP3 authentication failures. |
| plesk-dovecot | Scans for Dovecot IMAP, POP3, and Sieve authentication failures. |
| plesk-modsecurity | Scans for attacks against web applications detected by the ModSecurity Web Application Firewall. |
| plesk-panel | Scans for Plesk authentication failures. |
| plesk-qmail | Scans for qmail SMTP authentication failures. |
| plesk-roundcube | Scans for Roundcube webmail authentication failures. |
| plesk-wordpress | Scans for WordPress authentication failures. |
| postfix | Scans for Postfix SMTP and SASL authentication failures. |
| proftpd | Scans for ProFTPD authentication failures. |
| recidive | Scans for IP addresses repeatedly banned by Fail2Ban. |
| sshd | Scans for SSH authentication failures. |