DKIM, SPF, and DMARC Protection and ARC Support
概要: Plesk supports modern anti-spam mechanisms used to validate the identity of mail senders. Namely, DKIM, SPF, DMARC, and ARC.
In this topic, you will learn how to configure DKIM, SPF, and DMARC protection in Plesk. You will also learn how ARC support is implemented in Plesk for Linux.
Here is a short summary of the three mechanisms described in this topic and what they do:
- DKIM (DomainKeys Identified Mail) 方案用于将域名身份与发送信息建立关联,并通过密码验证方式验证与接收信息相关联的域名身份。
- SPF (Sender Policy Framework) 方案用于阻止伪造发件人地址,例如使用伪造的发件人地址。该方案允许邮件服务器检查发自某个域名的接收邮件是否来自该域名管理员授权的某个主机。此外,Plesk 会使用 SRS (Sender Rewriting Scheme) 以保证被转发信息可以通过 SPF 检查。
- DMARC (Domain-based Message Authentication, Reporting and Conformance) 技术可扩展 SPF 和 DKIM 方案的功能。DMARC 执行策略以根据 DKIM 和 SPF 检查的结果来处理邮件信息。
- ARC (Authenticated Received Chain) is a technology that enables intermediate mail servers (for example, mailing lists and mail forwarding services) to store an email’s authentication results using special headers. This helps the destination mail server validate the email if its SPF and DKIM records are made invalid by the intermediate mail server’s processing.
要使用这些方案对邮件服务器的要求如下:
| 邮件服务器 | DKIM | SPF* | SRS | DMARC | ARC |
|---|---|---|---|---|---|
| Postfix (Linux) | ➕ | ➕ | ➕ | ➕ | ➕ |
| Qmail (Linux) | ➕ | ➕ | ➖ | ➕ | ➕ |
| MailEnable Professional (Windows) | ➕ | ➖ | ➖ | ➖ | ➖ |
| MailEnable Standard (Windows) | 9.16 或更新版本 | ➖ | ➖ | ➖ | ➖ |
| SmarterMail (Windows) | ➕ | ➖ | ➕ | ➕ | ➖ |
| IceWarp (Windows) | ➕ | ➖ | ➕ | ➖ | ➖ |
在该表格中,‘+’ 表示 Plesk Obsidian 支持的所有版本都支持该方案。‘-‘ 表示不支持该方案。
注解: *在上表中,SPF支持是指发送邮件的SPF。Linux邮件服务器标记有‘+’,因为Plesk for Linux 支持接收和发送邮件的SPF。Windows邮件服务器标记有“-”,因为Plesk for Windows只支持发送邮件的SPF。
DKIM
为域名启用 DKIM 将特殊的信息头附加到发自该域名的每个电子邮件。此信息头包含加密私钥。收件人邮件服务器会使用公钥核实电子邮件是否发自该域名且是否有人在传输过程中篡改电子邮件内容。没有信息头的电子邮件将被检测认定为不真实信息。
为了提供 DKIM 支持,Plesk 会使用外部库 (Linux) 或 Plesk 提供的邮件服务器(Windows) 的功能。
启用或禁用服务器上的 DKIM
默认在 Plesk 中启用 DKIM。若要禁用 DKIM 或仅保留用于发送和接收邮件,请转到 工具与设置 > 邮件服务器设置(在 “邮件” 下),向下滚动到 “DKIM 垃圾邮件防护” 部分,清空以下当中的一个复选框或两个都清空:
- “允许签名发送邮件”。此选项使客户能够在每个域的基础上管理发送邮件的DKIM签名
- (Plesk for Linux) “核查接收邮件 ” 。该选项会为所有接收邮件启用 DKIM 检查功能。会检查所有的信息,如果检查失败,则会使用特殊的标头进行标记。
注解: 如果启用了 DMARC 则无法对接收邮件禁用 DKIM 检查。
启用域名的 DKIM
若在服务器上启用了DKIM签名,那么在Plesk中具有DNS和邮件主机的新域默认会使用DKIM签名发送邮件。
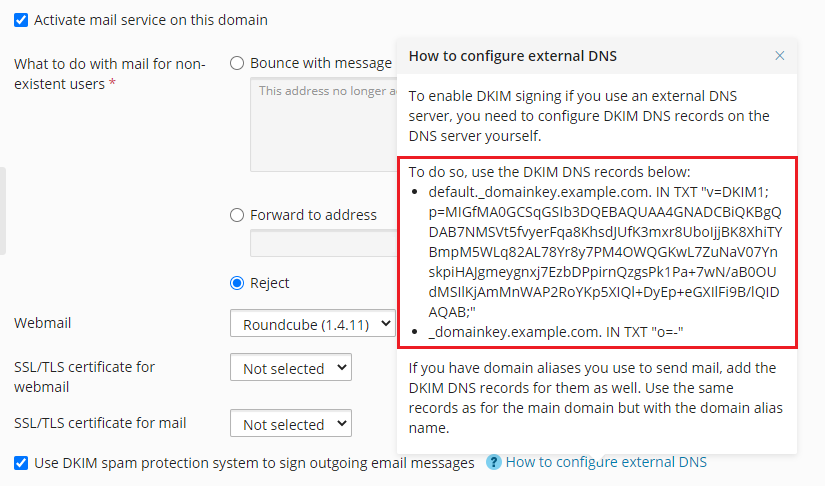
默认情况下,使用外部DNS服务器的域无法启用DKIM。使用DKIM签名发送邮件意味着Plesk会将以下两条记录添加到域的DNS区域(example.com代表您的域名):
-
default._domainkey.example.com包含已生成密钥的公共部分。 -
_ domainkey.example.com包含 DKIM 策略。您可以编辑该策略。
与Plesk中托管的域不同,Plesk无法将这些记录添加到使用外部DNS服务器的域中。对于这些域,您需要手动启用DKIM。
要为使用外部DNS服务器的域启用对发送邮件进行DKIM签名,请如下操作:
-
转到 网站与域名 > 您的域名 > “邮件” 标签 > 邮件设置。
-
保持选中”使用 DKIM 垃圾邮件防护系统签名发送电子邮件信息”复选框。
-
点击 “如何配置外部的 DNS” 提示。复制您在此看到的两个 DNS 记录然后将其添加到 DNS 服务器。
注解: 若您有用于发送邮件的域名别名,请同时为其添加 DKIM DNS 记录。请将用于主域名的相同记录用于域名别名。
SPF 和 SRS
SPF(发件人策略框架)是用于阻止发件人地址伪造(例如使用伪造的发件人地址)的一个方案。SPF 允许域名管理员设置策略,授权特定主机从域名发送邮件。接收邮件的服务器会检查来自某域名的收件是否发自域名管理员授权的主机。SPF 基于发件人的 DNS 区域中的管理员指定的规则。
在 Plesk 中,您可以在 DNS 记录中指定规则来设置用于发送邮件的 SPF 策略。另外在 Linux 上,SPF 还默认检查接收邮件。
当设置了 SPF 时,邮件服务器则会使用以下算法步骤检查接收的邮件:
-
阅读本地规则。
本地规则是垃圾邮件过滤器使用的本地规则。本地规则示例如下:
a:test.plesk.com。 -
搜索发件人的 DNS SPF 记录(如果有)。
SPF 记录示例如下:
example.com. TXT v=spf1 +a +mx -all -
将本地规则和 SPF 记录合并到产生的策略中。
在我们的示例中,产生的策略将是
example.com. TXT v=spf1 +a +mx +a:test.plesk.com -all。注解: If the mail server detects no SPF record, local rules will be ignored as well.
-
根据由上一步操作所生成的策略来检查邮件。
-
阅读猜测规则。
猜测规则是全局规则,会覆盖 SPF 记录。猜测规则示例如下:
v=spf1 +a/24 +mx/24 +ptr ?all。 -
只根据猜测规则检查邮件。
-
对比两个检查的结果:根据产生的策略进行的检查(第4步)和只根据猜测规则进行的检查(前一步)。应用其结果更为宽容的检查。
若要为发送邮件设置一个 SPF 策略,请如下操作:
Go to Tools & Settings > DNS Settings (under “General Settings”) and edit the TXT DNS record related to SPF. This DNS record is always present in the server-wide DNS template. Here is an example of SPF record created by Plesk:
example.com. TXT v=spf1 +a +mx +a:test.plesk.com -all
该记录的各个部分所表示的意思如下:
| 部分 | 描述 |
|---|---|
v=spf1 |
域名使用版本 1 的 SPF。 |
+a |
来自 “A” 记录的所有主机都被授权发送邮件。 |
+mx |
来自 “MX” 记录的所有主机都被授权发送邮件。 |
+a:test.plesk.com |
域名 test.plesk.com 被授权发送邮件。 |
-all |
所有其它域名未被授权发送邮件。 |
了解更多有关 SPF DNS 记录的语法的信息。策略符号可在 RFC7208查找。
(Plesk for Linux) 若要配置 SPF 检查接收邮件:
-
转到 工具与设置 > 邮件服务器设置(在 “邮件” 下)并向下滚动到 “SPF 垃圾邮件防护” 部分。
-
从 SPF 检查模式下拉框中选择一个选项以指定当 SPF 应用本地和推测规则时应如何处理电子邮件:
- 只创建 Received-SPF 标头信息,不屏蔽 - 不管 SPF 检查的结果接受所有的接收信息。
- DNS查找出现问题时,使用临时错误通知 - 不管 SPF 检查的结果,即使因 DNS 查找问题导致 SPF 检查失败,仍接受所有的接收信息。
- SPF解析为“失败”(拒绝)时,退信 - 拒收发自未被授权使用域名的发件人的信息。
- SPF解析为“软失败”时,退信 - 拒收发自未被SPF系统识别为授权发件人的或因域名没有发布SPF记录而未被授权的发件人的信息。
- SPF解析为“中性”时,退信 - 拒收发自未被SPF系统识别为授权发件人的或因域名没有发布SPF记录而未被授权的发件人的信息。
- SPF没有解析为“通过”时,退信- 拒收因任何原因而未通过SPF检查的信息(例如,收件人的域名未执行SPF而SPF检查返回”未知”状态。)
-
如要指定本地规则,请在 SPF 本地规则 框内输入您需要的规则。例如: include:spf.trusted-forwarder.org 。
-
您还可以在 SPF 猜测规则 框内指定猜测规则。
例如: v=spf1 +a/24 +mx/24 +ptr ?all
-
要指定当邮件被拒绝时返回给 SMTP 发件人的任意错误通知,请在 “SPF 解释文本” 框中键入该通知。
如果未指定任何值,默认的文本将会做为通知发送出去。
-
要完成设置,请单击 “确定” 。
(Plesk for Linux) 若要禁用 SPF 检查接收邮件,请如下操作:
- 进入 工具与设置 > 邮件服务器设置(在 “邮件” 下)。
- 在 “DMARC” 部分,清空 “启用 DMARC 检查接收邮件” 复选框(如已勾选)。
- 在 SPF 垃圾邮件防护 部分请清空 启用 SPF 垃圾邮件防护检查接收邮件 复选框然后点击 确定。
使用 SRS
除了SPF,Plesk中的某些邮件服务器还支持 SRS (Sender Rewriting Scheme),该机制是在转发邮件(被转发的邮件仍继续要符合SPF) 时,支持覆写发件人地址。SRS 可帮助确保在使用SPF时发送信息。
当从 Plesk 托管的邮箱转发信息时会自动使用 SRS。
为了提供 SRS 功能,Plesk 会使用外部库 (Linux) 或邮件邮件服务器软件 (Windows) 的功能。
DMARC
DMARC (Domain-based Message Authentication, Reporting and Conformance) 是扩展 SPF 和 DKIM 发件人策略的功能的一项技术。DMARC 执行策略以根据 DKIM 和 SPF 检查的结果来处理邮件信息。该技术基于在发件人DNS区域中指定的规则。
在Plesk中,您可以通过在DNS记录中指定规则来为发送邮件设置DMARC策略。
注解: 在使用 SmarterMail 的 Plesk for Linux 和 Plesk for Windows 中,DMARC也会在默认检查接收邮件。
若要为发送邮件设置自定义的 DMARC 策略,请如下操作:
- 进入 工具与设置 > DNS 设置(在 “常规设置”下)。
- 编辑与 DMARC 策略相关的 DNS 记录。这些 DNS 记录总是会出现在 服务器级的 DNS 模板 中。相反,当在域名上激活 DKIM 时,与 DKIM 相关的 DNS 记录会被添加到该域名的 DNS 区域中。
例如,Plesk默认的 DMARC 策略在以下记录中指定:
_dmarc.<domain>. TXT v=DMARC1; adkim=s; aspf=s; p=quarantine
根据此策略,接收邮件服务器应将未通过DKIM和SPF检查的电子邮件进行隔离。隔离意味着将电子邮件移动到垃圾邮件文件夹,并将其标记为可疑。您可以指定一个更严格的策略。但是,接收服务器仍可以自由地将其自己的策略应用于接收邮件。
域也有自己单独的DMARC策略,客户可以编辑这些策略。在Plesk中拥有DNS和邮件主机的新域默认会启用DMARC隔离策略。
若要禁用 DMARC 检查接收邮件,请如下操作:
- 进入 工具与设置 > 邮件服务器设置(在 “邮件” 下)。
- 在 DMARC 部分,清空 “启用 DMARC 检查接收邮件” 复选框然后点击 确定。
(Plesk for Linux) ARC
ARC (Authenticated Received Chain) is a technology that enables intermediate mail servers to add an additional layer of authentication to emails that are forwarded or sent from a mailing list by adding extra headers to emails. This is so that the final receiving mail server may be able to (but does not have to) treat an email as legitimate even if it fails its SPF, DKIM, and/or DMARC checks.
注解: ARC is supported on all Plesk Obsidian 18.0.58 and later servers running the Postfix or qmail mail servers. At the moment, ARC is only supported in Plesk for Linux, because none of the mail servers supported in Plesk for Windows have ARC support.
注解: The ARC support implementation in Plesk satisfies the Google requirement to add ARC headers to forwarded mail for senders who send 5000 or more messages a day to Gmail accounts.
局限性
- ARC headers are not added to mail sent to a mailing list.
- Plesk does not validate the ARC headers for incoming mail.
Enabling ARC Support
(Plesk for Linux) To enable ARC support on your server:
- 登录到 Plesk。
- 进入 工具与设置 > 邮件服务器设置(在 “邮件” 下)。
- Under “DKIM spam protection”, select the “Allow signing outgoing mail” checkbox.
- (Recommended) Under “SPF spam protection”, select the “Enable SPF spam protection to check incoming mail” checkbox.
- (Recommended) Under “DMARC”, select the “Enable DMARC to check incoming mail” checkbox.
- 点击 确定 。
ARC headers can now be added to outgoing mail forwarded via the Plesk forwarding feature or sent by the autoresponder.
Once ARC support is enabled on your server, ARC can be enabled for individual mail domains.
注解: For the ARC signatures to be valid, the DNS records required for DKIM to work must be configured properly for the domain hosting the forwarding mail account.
(Plesk for Linux) To enable ARC for a domain:
- 登录到 Plesk。
- Go to Websites & Domains, find the domain hosting the mail account, go to the “Mail” tab, and then click Mail Settings.
- Select the “Use DKIM spam protection system to sign outgoing email messages” checkbox, and then click OK.
ARC headers will now be added to outgoing mail forwarded via the Plesk forwarding feature or sent by the autoresponder by any of the mail accounts hosted on the domain.