Installing Certificates
The install operation is used to install an SSL/TLS certificate to the server certificate repository or to a specified subscription repository. Please note that this operation only installs a certificate to a repository, it does not enable SSL/TLS support for sites, therefore, it does not make sites available via the HTTPS protocol.
Request Packet Structure
A request XML packet installing an SSL/TLS certificate includes the install operation node:
<packet>
<certificate>
<install>
...
</install>
</certificate>
</packet>
The install node does not have a separate data type, it is nested
within type CertificateActionRequest (certificate_input.xsd). The
install node has the following graphical representation:
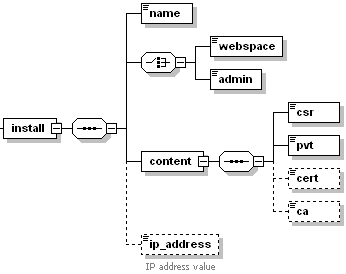
Note: The interactive schema navigator for all request packets is available here: http://plesk.github.io/api-schemas/1.6.9.1/agent_input.svg.
-
name, required
Specifies the name under which the certificate will be known in the repository and in Plesk. Data type: string.
Either the webspace or admin elements are required.
-
webspace, optional
Specifies the subscription to which the certificate is installed. Data type: string.
-
admin, optional
Specifies that the certificate is installed to the server repository. Data type: none.
-
content, required
Contains all data constituting the certificate. Data type: none.
-
csr, required
Specifies the certificate CSR (certificate signing request). Data type: string.
-
pvt, required.
Specifies the certificate private key. Data type: string.
-
cert, optional
Contains the certificate body. Data type: string.
-
ca, optional
Contains the certificate authority body. Data type: string.
-
ip_address, optional
Specifies IP address to which the certificate will be assigned when it is installed to server repository. This assignment means that sites hosted on this IP address, in case SSL/TLS support is enabled for them, will display this certificate when accessing the sites. Data type: ip_type (
common.xsd).
Note: When creating request packets, put nodes and elements in the order they follow in the packet structure.
Response Packet Structure
The install node of the output XML packet is structured as follows:
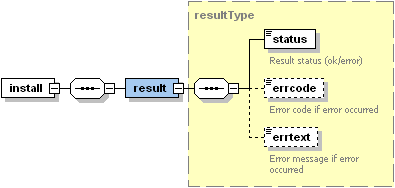
Note: The interactive schema navigator for all response packets is available here: http://plesk.github.io/api-schemas/1.6.9.1/agent_output.svg.
-
result, required
Wraps the response retrieved from the server.
-
status, required
Specifies the execution status of the operation. Data type: string. Allowed values: ok | error.
-
errcode, required if the operation fails
Returns the error code. Data type: unsignedInt.
-
errtext, required if the operation fails
Returns the error message . Data type: string.
Installing certificate
This packet installs to the server repository a CA certificate that will be known in Plesk under the name common and will be assigned to IP address 192.0.2.14 upon the installation.
<packet>
<certificate>
<install>
<name>common</name>
<admin/>
<content>
<csr>-----BEGIN CERTIFICATE REQUEST-----
MIICwTCCAakCAQAwfDELMAkGA1UEBhMCVVMxEDAOBgNVBAgTB2dlb3JnaWExEDAO
...
ZZbX2Vbskz0WJ1IcxsfWDJ/HFdho7GrrD/wujNpwkTPc3xe2AHcfQX8c/92xyra/
kdzxsDdFD7IwA5bBWGm8QwlL9yWuDPiZ8vSGw96D/Qije9UVkA==
-----END CERTIFICATE REQUEST-----</csr>
<pvt>-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAyxfczy4HqgwOI6yxEa+dLaMLe5zC0ijcawsha8oFtJlxv/DM
...
Bxq2AbPRohXasWEAdfgfss1mcwX9xnKO/DhnxXE8KVFXKVehGmUth0WqA5qtL4xD
h4hm3V7DcMqYbVzpmlWXFz5Is1fIflAhlfeX4h3s1rirTj+T6hODVf4=
-----END RSA PRIVATE KEY-----</pvt>
<cert>-----BEGIN CERTIFICATE-----
MIIDiTCCAnECBETUDecwDQYJKoZIhvcNAQEEBQAwgYgxCzAJBgNVBAYTAlJVMQww
...
i3Cm04Gz1h9W/yzkcYCqiwUMIzSgUSBLn0hBeTid1u/NaDtic776YGuyaI+/
-----END CERTIFICATE-----</cert>
<ca>
-----BEGIN CERTIFICATE-----
MIIEjDCCA3SgAwIBAgIJAL4AGzKhkL5wMA0GCSqGSIb3DQEBBQUAMIGKMQswCQYD
...
2Q/sUQaWgJhe4RDoth6w7E9GE8733WGhC1mIjxyJMx4vmu4ofLAwN6XUzJJ3eC7s
P34vOGq/sqxG/U+BbUu71A==
-----END CERTIFICATE-----
</ca>
</content>
<ip_address>192.0.2.14</ip_address>
</install>
</certificate>
</packet>
Installing several certificates
This packet installs two certificates to repositories of subscriptions example.com and sample.net.
<packet>
<certificate>
<install>
<name>common</name>
<webspace>example.com</webspace>
<content>
<csr>-----BEGIN CERTIFICATE REQUEST-----
MIIBujCCASMCAQAwejELMAkGA1UEBhMCQUYxDjAMBgNVBAgTBVN0YXRlMQ0wCwYD
...
hmmgZf1vgJN7waDZ/7GBG+ZySEnqHOnQo2cGPbZ7HaF2GTn67F5fHu52/HhtlPrt
5OLH+Ftv5Z1cy3kziqE=
-----END CERTIFICATE REQUEST-----</csr>
<pvt>-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQC7s14ervVsRk64NHKgHppXJCy4gMX/sdHxxlovg8tloYB5/OEL
...
yxyGPJUpXLgurEasPjCBAkA3AWOwcg2yYY/dQws81lHZd6I4l43PZtEiJ0C/k8tR
OmU2Co29ysy1fids1zwVXXuyYeaKVLqMipfl+O2TADyg
-----END RSA PRIVATE KEY-----</pvt>
</content>
</install>
<install>
<name>personal</name>
<webspace>sample.net</webspace>
<content>
<csr>-----BEGIN CERTIFICATE REQUEST-----
MIIBtDCCAR0CAQAwdDELMAkGA1UEBhMCUlUxDDAKBgNVBAgTA05TTzEMMAoGA1UE
...
BPYrHn47kOqsL05VLVMxhDjechzx0rML0g9l1zsZnPLibukKhR4NSWiNgVwACBt1
s3KuVqK0qSE=
-----END CERTIFICATE REQUEST-----</csr>
<pvt>-----BEGIN RSA PRIVATE KEY-----
MIICWwIBAAKBgQDSMFNv0uCVotZ5p06dcdj6omA+DbowFRMb4G5KMzskY9fUCIc0
...
mRygqkRBDP+KgjhECJjIkPuT0q7zHBam2TfcH4vAwA==
-----END RSA PRIVATE KEY-----</pvt>
</content>
</install>
</certificate>
</packet>