Setting Up the Password Strength Policy
summary: Weak passwords can easily be compromised by a brute-force attack. This allows threat actors some degree of access to the server, enabling them to deface hosted websites, send spam, steal information, and more.
You can configure a server-wide password strength policy that will enforce minimum password strength for all newly created passwords on the server. Strong passwords make brute-force attacks impractical or even impossible to carry out.
Password strength is a measure of a password’s resistance against guessing or brute-force attacks. It depends on a number of factors, such as:
- Password length.
- Whether the password includes both lower and upper case letters.
- The number of various characters included in the password (numbers, special characters, and more).
- Whether the password includes one or more dictionary words.
If users set weak passwords (for example, because they are easier to remember), they may inadvertently make the server vulnerable to attack. For example:
- If a mailbox password is compromised, the attacker can use the mailbox to send out spam, which may result in your server’s IP address being added to DNS Blackhole lists.
- If a system user password is compromised, the attacker can insert malicious code into the customer’s websites.
All of that can lead to financial and reputational damage, as well as data loss.
To prevent users from setting weak passwords, you can configure a server-wide password strength policy. The policy applies to many (but not all) passwords a user can set in Plesk. Whenever a Plesk user sets or changes a password, they are required to adjust the password until it meets the requirements of the password strength policy currently in effect.
Note: The password strength policy does not apply to passwords automatically generated by Plesk. Plesk always generates “very strong” passwords. This behavior is by default and cannot be changed.
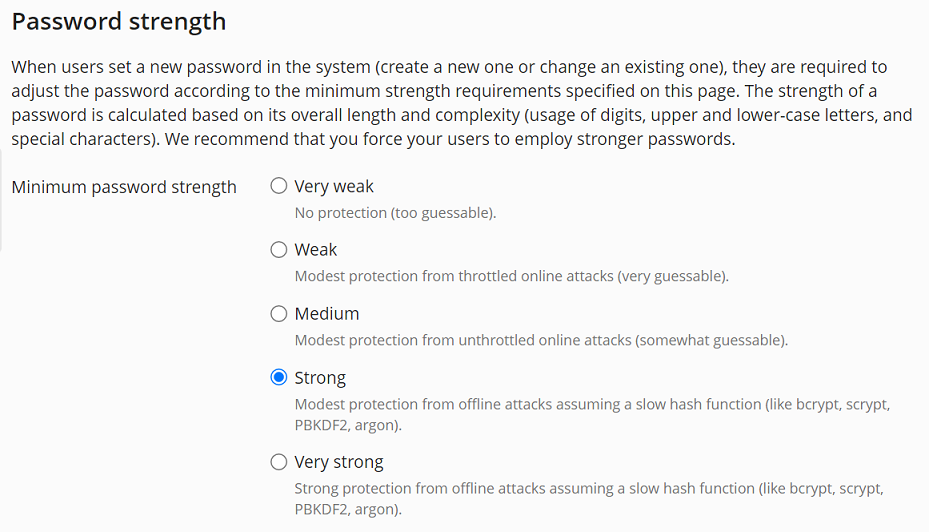
You can choose from five password strength levels ranging from “Very weak” to “Very strong”. The stricter the policy, the less are the chances that a user’s password would be vulnerable to a brute-force attack.
The way Plesk generates strong passwords and evaluates the strength of a password closely matches that of the popular third party password generators. This way, you can be sure that a strong password generated, for example, by 1Password, will be treated as such by Plesk. Learn how Plesk calculates password strength.
By default, the password strength policy is set to “Strong”. You may wish to apply a weaker policy if, for example, you use a third party password generator whose passwords are not validated as strong enough by Plesk.
Note: Changing the minimum password strength has no effect on passwords that have already been set. The change will only affect passwords that are set after the minimum password strength has been changed.
The password strength policy is applied to the following passwords:
- Passwords used to log in to Plesk.
- Subscription system users’ passwords.
- Database users’ passwords.
- Mailbox passwords.
The password strength policy is not applied to the following passwords:
- Passwords for applications hosted in Plesk (for example, WordPress, Joomla!, and so on).
- Passwords for services managed by Plesk (Git, Docker).
- Backup encryption passwords.
- Remote backup storage passwords.
To change the password strength policy:
- Go to Tools & Settings > Security Policy (under “Security”), and then scroll down to the “Password strength” section.
- Under “Minimum password strength”, select the radio button corresponding to the desired password strength policy.
- Click OK.
The new password policy is now in effect and will be applied every time a password the policy applies to is set or changed.