使用 SSL It! 擴展保護連接的安全
概要: The SSL It! extension helps you secure hosted websites with both free and paid SSL/TLS certificates.
In this topic, you will learn how to get free SSL/TLS certificates, how to buy paid certificates, how to upload certificates from a file, and how to secure hosted websites with any of those.
You will also learn how to harden the connections to hosted websites, and how to gauge the effectiveness of the SSL protection of hosted websites. If you are a Plesk administrator, you will also learn how to configure what SSL/TLS certificates are available to your customers from the SSL It! interface.
SSL It! 擴展會提供一個介面,通過該介面,可使用由可信的證書機構 (CA) Let’s Encrypt 和 DigiCert(Symantec、GeoTrust 和 RapidSSL 品牌)簽發的 SSL/TLS 證書或任何其它所選的 SSL/TLS 證書保護網站的安全。使用該擴展,您還可以執行以下操作::
- 通過從 HTTP 重定向到 HTTPS 增強網站訪客的安全度。
- 通過禁止 web 瀏覽器存取使用 HTTP 不安全連接的網站來保護網站訪客。
- 使用 OCSP 裝訂保護網站訪客的隱私並提高網站性能。
- 讓使用 SSL/TLS 證書加密的連接在使用 Mozilla 生成的協定和密碼時更安全。
開始使用 SSL It!
請考慮以下因素:
- SSL It! 擴展默認已安裝。
- 若要利用所有的 SSL It! 功能,請確保還安裝了最新版的 DigiCert SSL 和 Let’s Encrypt 擴展。
若要管理域名的 SSL/TLS 證書,請轉到 網站與域名 > 您的域名。您可以看到 「SSL/TLS 證書」下域名當前的安全狀態。
使用 SSL/TLS 證書保護網站的安全
通過 SSL It! 擴展,您可以使用免費的和付費的 SSL/TLS 證書(目前只能使用 DigiCert 的證書)以及您已有的 SSL/TLS 證書保護網站的安全。
若要使用 Let’s Encrypt 免費的 SSL/TLS 證書保護網站的安全,請如下操作:
-
轉到 網站與域名 > 您的域名 > SSL/TLS 證書。
-
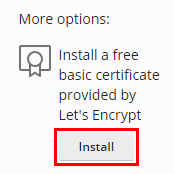
在 「更多選項」 下,點按 安裝:
-
指定將用於緊急通知和丟失金鑰恢復的電郵地址。
-
選擇除了主域名之外還需保護的域名:
-
保護主域名的安全。只保護主域名。如果您只想保護 web 郵箱的安全,可以清空該核取方塊。
-
保護萬用字元域名(包括 www 和 web 郵箱)的安全。保護 www 子域名和/或域名別名和 web 郵箱。
-
包括域名的一個“www”子域名和每個選定的別名。保護www子域名和/或域名別名。
-
保護此域名上的 web 郵箱的安全。保護 web 郵箱。
-
Assign the certificate to the mail domain. Secure the mail server connections for this domain. Useful if the mail server is not protected with an SSL/TLS certificate, or if the certificate securing the mail server cannot be verified.
If you have the www subdomain and/or domain aliases, we recommend that you also select the Include a 「www」 subdomain for the domain and each selected alias checkbox.
-
-
點按 免費獲取。
將會簽發一個 Let’s Encrypt 的 SSL/TLS 證書並自動安裝。
備註: 如果您使用 Let’s Encrypt 的 SSL/TLS 證書保護域名的安全然後向訂閱添加新的域名、子域名、域名別名或 web 郵箱,可重新簽發 Let’s Encrypt 的 SSL/TLS 證書以自動使用 SSL It! 保護它們的安全。具體操作是,轉到 網站與域名 > 您的域名 > SSL/TLS 證書 啟用保護網站的安全選項。
若要獲取付費的 SSL/TLS 證書,請如下操作:
-
轉到 網站與域名 > 您的域名 > SSL/TLS 證書。
-
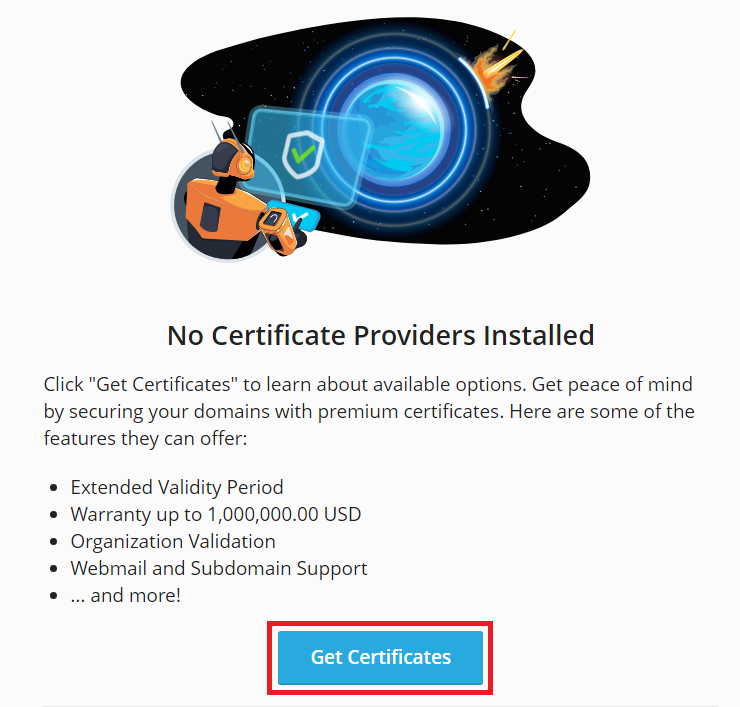
若要獲取可用證書的列表,請按一下“獲取證書”:
-
選擇您要購買的SSL/TLS證書,然後按一下證書表單中的購買按鈕.
備註: To find an appropriate certificate, you can do the following:
- Filter the available certificates. You can apply the Recommended, Wildcard, and For organization use filter sets.
- Read more about a certificate (its validity period, validation type, and so on) by clicking the Learn more button in the certificate’s form.
-
在Plesk線上商店的快顯視窗中,填寫您的位址、支付資訊,然後購買證書。
-
關閉快顯視窗。
-
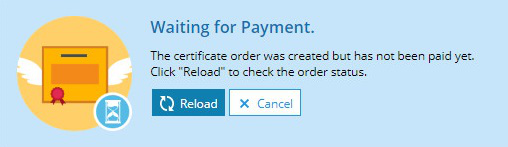
等待 Plesk 更新付款狀態或通過點按重新載入手動將其更新。Plesk每小時自動更新一次支付狀態。
-
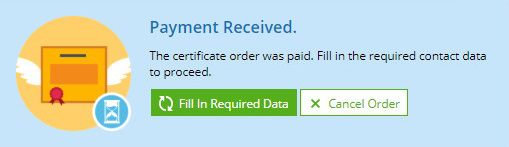
付款處理後,點按 填寫必填資料。
-
填寫必填聯繫資訊然後點按 確定。
Plesk 現在即自動創建證書簽名請求 (CSR) 然後接收和安裝 SSL/TLS 證書。根據不同類型的 SSL/TLS 證書,可能需要一定時間。您可以點按 重新載入 手動更新 SSL/TLS 證書狀態或等候 Plesk 自動將其更新(Plesk 會每小時檢查 SSL/TLS 證書狀態一次)。
備註: 某些類型的 SSL/TLS 證書(例如 EV)需要您額外執行一些操作。您可能需要接聽電話或回復電子郵件,同時還需提交必要的檔,這樣 CA 才可以驗證您的應用程式。
SSL/TLS 證書安裝好後,網站與域名 > 您的域名 > SSL/TLS 證書 螢幕將會顯示有關已安裝的 SSL/TLS 證書(名稱、證書機構、電郵地址,等等)、已安全保護的元件和其它選項(」從 http 重定向到 https」、」HSTS」,等等)的資訊。
通過 CLI 保護網站安全
您還可以通過 CLI 使用萬用字元 SSL/TLS 證書來保護網站安全。執行以下CLI命令:
plesk ext sslit --certificate -issue -domain <domain_name> -registrationEmail <email> -secure-domain -wildcard
然後
plesk ext sslit --certificate -issue <domain_name> -registrationEmail <email> -continue
第一個命令會創建一個萬用字元證書訂單,而第二個命令會完成訂單並簽發證書。
上傳 SSL/TLS 證書
您已經有一個用於保域名安全的證書。
- 您已經有一個用于保護域名安全的證書。
- 您想要安裝無法通過 SSL It! 獲取的證書。
若要上傳 SSL/TLS 證書,請如下操作:
-
轉到 網站與域名 > 您的域名 > SSL/TLS 證書 然後點按 上傳。
-
找到您要上傳的 SSL/TLS 證書的
.pem文件然後點按 打開。
SSL/TLS 證書將自動在域名上安裝。
續訂更新已安裝的 SSL/TLS 證書
為了您的網站能夠得到持續有效的安全保護,您需要按時續訂更新已安裝的 SSL/TLS 證書。SSL It! 擴展會幫助您實現此目的。
SSL It! 會在證書到期前 30 天自動續訂更新 Let’s Encrypt 和 DigiCert 免費的 SSL/TLS 證書。
SSL It! 無法自動續訂更新付費的 SSL/TLS 證書,但是您可以:
- 手動重新簽發這些證書。
- 讓 SSL It! 使用 Let’s Encrypt 免費的證書自動替換已到期的 SSL/TLS 證書。
若要重新簽發付費的 SSL/TLS 證書,請如下操作:
-
轉到 網站與域名 > 使用快要到期的付費 SSL/TLS 證書保護安全的域名 > SSL/TLS 證書。
-
點按 重新簽發證書。然後會自動將您重定向到 Plesk 線上商店。
-
在Plesk線上商店的快顯視窗中,填寫您的位址、支付資訊,然後購買證書。
-
關閉快顯視窗。
-
等待 Plesk 更新付款狀態或通過點按重新載入手動將其更新。Plesk每小時自動更新一次支付狀態。
-
付款處理後,點按 填寫必填資料。
-
填寫必填聯繫資訊然後點按 確定。
Plesk 現在即自動創建證書簽名請求 (CSR) 然後接收和安裝 SSL/TLS 證書。根據不同類型的 SSL/TLS 證書,可能需要一定時間。您可以點按 重新載入 手動更新 SSL/TLS 證書狀態或等候 Plesk 自動將其更新(Plesk 會每小時檢查 SSL/TLS 證書狀態一次)。
若要使用 Let’s Encrypt 免費的證書自動替換已到期的付費 SSL/TLS 證書,請如下操作:
- 轉到 網站與域名 > 使用快要到期的付費 SSL/TLS 證書保護安全的域名 > SSL/TLS 證書。
- 開啟 保護網站的安全。
現在,當您的付費 SSL/TLS 證書到期時,SSL It! 會自動簽發一個 Let’s Encrypt 的免費 SSL/TLS 證書保護屬於訂閱的域名、子域名、域名別名和 web 郵箱的安全。通常在 SSL/TLS 證書到期後不到一個小時自動實現。
增強網站和已加密伺服器連接的安全性
僅僅使用來自可信 CA 的有效 SSL 證書保護網站的安全不足以獲得全面的保護。SSL 是一種複雜的技術,有很多功能(金鑰加密演算法、安全密碼、HSTS,等等),這些功能可以:
- 增強網站訪客的安全性。
- 提高網站性能。
- 強化所有伺服器加密連接的安全性
啟用這些功能可以提高網站的搜尋引擎排名:
- 從 http 重定向到 https會設定永久的、SEO 安全 301 重定向,將網站和 web 郵箱從不安全的 HTTP 版永久重定向到安全的 HTTPS 版。
- HSTS 會禁止 web 瀏覽器通過不安全的 HTTP 連接存取網站。
- OSCP 會令 web 伺服器從 CA 而不是訪客的瀏覽器請求網站證書的狀態(可以是良好、撤銷或未知)。
- Mozilla 支援的 TLS 版本和密碼強化了 SSL/TLS 證書保護的連接(網站、郵件、Plesk,等等)。
警示: 在開啟這些功能前,請確保您的網站可以通過 HTTPS 進行存取。否則,訪客在存取您的網站時會遇到麻煩。
備註: 如果您已手動在您的 web 伺服器中設定了 HSTS 或 OCSP 裝訂,請在 SSL It!.中打開 HSTS or OCSP 裝訂之前刪除這些自訂設定。
若要增強網站和已加密伺服器連接的安全性,請如下操作:
-
使用可信 CA 的有效 SSL/TLS 證書保護網站的安全。
-
轉到 網站與域名 > 您的域名 > SSL/TLS 證書。
-
如果您已從 Plesk 早期版本升級到 Plesk Obsidian,請打開 從 http 重定向到 https。默認此重定向也將會應用於 web 郵箱。在 Plesk Obsidian 乾淨的安裝實例上,預設已為域名和 web 郵箱打開重定向。
備註: 如果您的web郵箱沒有有效的SSL/TLS證書保護,或者您沒有任何web郵箱,請按一下滑塊圖示,清空**應用到web郵箱**核取方塊,然後按一下**應用**。
-
備註: 如果您的 SSL/TLS 證書早於Max-age 期限到期但是您仍想要使用 HSTS,我們建議您啟用 「保護網站的安全」。然後當 SSL/TLS 證書到期時,SSL It! 將自動簽發 Let’s Encrypt 的免費證書用來保護屬於訂閱的域名、子域名、域名別名和 web 郵箱。網站將持續得到安全保護且 HSTS 將繼續工作運行。
-
打開 OCSP 裝訂。
一旦強化了網站和伺服器的 SSL 安全性,即可評估網站的 SSL 安全性。
備註: 您還可以通過 CLI 啟用 HSTS和OCSP。例如,若要為已經使用 SSL/TLS 證書保護安全的域名 example.com 啟用 HSTS,請運行以下命令:
plesk ext sslit --hsts -enable -domain example.com -max-age 6months
若要為同一域名啟用OCSP,請運行以下命令:
plesk ext sslit --ocsp-stapling -enable -domain example.com
若要瞭解通過 CLI 使用 SSL It! 的資訊,請運行 plesk ext sslit --help 命令。
啟用 HSTS
打開 HSTS。
請確保保護您網站的 SSL/TLS 證書在Max-age時段內有效。對子域名和 web 郵箱子域名執行同樣的操作。
警告: 如果SSL/TLS證書在 Max-age 時段之前過期,並且 HSTS 已打開,則訪問者將無法存取您的網站。
如果您的子域名未使用有效的 SSL/TLS 證書進行安全保護或者您沒有任何子域名,請清空 包括子域名 核取方塊。
如果您的 web 郵箱子域名尚未使用有效的 SSL/TLS 證書保護或您還沒有任何 web 郵箱,請清空 包括 web 郵箱 核取方塊。
點按 啟用 HSTS。
啟用 Mozilla 支援的 TLS 版本和密碼
- 轉到 擴展 > 我的擴展 標籤 > 點按 SSL It! 旁的 打開。
- 按一下 設定 。
- 在 Mozilla 支援的 TLS 版本和密碼下,開啟切換。
- 保留 中間(推薦),然後點按 啟用並同步。
- 若要保持當前狀態,請每隔幾個月點按即刻同步一次。
評估網站的 SSL 的安全性
流行的搜尋引擎(例如 Google)會給有更好 SSL 保護的網站更高排名。在 SSL It! 擴展中,您可以運行最流行的測試服務,Qualys SSL Labs,以實現:
- 檢查您網站的 SSL 保護有多好。
- 查看哪些可以提升。
- 獲得 A+,最高評分(必要時強化 SSL 保護後)。
若要評估網站的 SSL 的安全性,請如下操作:
- 轉到 網站與域名 > 您的域名 > SSL/TLS 證書。
- 點按運行 SSL Labs 測試。
將在新的標籤中打開 Qualys SSL Labs 網站,然後自動開始測試。等測試結束後即可獲得您的評分。這可能需要幾分鐘的時間。
如果您使用可信 CA 的有效 SSL/TLS 證書保護網站的安全,且打開了 SSL It! 提供的所有安全增強功能,最有可能得到 A+ 的評分。
自訂 SSL It! 提供的 SSL/TLS 證書列表
SSL It! 使從各種供應商處訂購SSL/TLS證書成為可能。您可以選擇您、您的客戶和代理商在 SSL It! 介面中可見哪些證書。通過安裝(啟用)或移除(禁用)SSL It! 外掛程式來完成此操作,促成 SSL It! 和某個特定供應商整合。
添加從特定供應商訂購SSL/TLS證書的功能:
- 轉到擴展,並在搜索欄位中鍵入與所需供應商對應的外掛程式擴展的名稱。
- 安裝擴展。如果擴展已經安裝,請確保沒有將其禁用,並在必要時將其啟用。
您、您的客戶和代理商將只能在 SSL It! 介面中看到該供應商出售的證書。
移除從特定供應商訂購SSL/TLS證書的功能:
- 轉到擴展>我的擴展,並找到與所需供應商對應的外掛程式擴展。
- 移除或禁用擴展。
您、您的客戶和代理商將不能在 SSL It! 介面中看到該供應商銷售的證書!這不會影響到已經從該供應商購買了SSL/TLS證書的客戶。
SSL It! 提高了證書簽發的概率
SSL It! 有一個默認功能,會大幅度降低因域名配置不相容而導致無法簽發 Let’s Encrypt SSL/TLS 證書的情況的發生。
當您從 Let’s Encrypt 獲取 SSL/TLS 證書時,其伺服器需要驗證您是否掌控證書中的域名。具體實現方式是,Let’s Encrypt 會使用 “challenges”:Let’s Encrypt 會給予一個 Plesk 放置於 http://<your_domain>/.well-known/acme-challenge/<token> 中的權杖文件。我們稱此目錄為通用 challenge 目錄。如此目錄無法存取,則會導致證書簽發失敗。此情況可能會因以下配置產生:
- 目錄已受一個密碼保護。
- 您要保護安全的網站被 “拒絕存取網站” 功能攔阻了。
- 不正確的 MIME 類型等等。
安裝時,即使檢測到了某些不相容的配置 SSL It! 也會確保支援並可存取通用 challenge 目錄。Plesk for Linux 和 Plesk for Windows 中預設啟用 “通用 challenge 目錄支援”功能。
如果需要,您可以運行以下命令通過 CLI 關閉該功能:
plesk ext sslit --common-challenge-dir –disable
但是,我們建議保持開啟“通用 challenge 目錄支援”功能。
若您已從更早的版本更新到 SSL It! 1.4.0,將會自動開啟“通用 challenge 目錄支援”,除非在 panel.ini 中禁用了 use-common-challenge-dir 設定。如果禁用了該選項,則需要運行以下命令手動開啟此支援:
plesk ext sslit --common-challenge-dir –enable
自 SSL It! 1.4.0 版本起 use-common-challenge-dir 設定已棄用。
防止客戶嘗試簽發萬用字元Let’s Encrypt 證書失敗
預設情況下,簽發萬用字元Let’s Encrypt 證書適用于客戶擁有的所有域名。但是,根據域名的DNS配置,簽發可能會成功或失敗。在 SSL It! 中,您可以為不能使用這些證書自動保護的域名隱藏簽發萬用字元Let’s Encrypt 證書的功能。
SSL It! 只能為將 Plesk 用作主控 DNS 伺服器的域名或與 Plesk同步的協力廠商 DNS 服務自動簽發萬用字元 Let’s Encrypt 證書。如果DNS服務沒有與Plesk同步,SSL It! 無法使用萬用字元Let’s Encrypt 證書保護域名安全。客戶嘗試簽發萬用字元Let’s Encrypt證書必然會失敗,這樣會導致產生客戶支援工單。為了減少支援工作負擔,您可以為其DNS記錄不在Plesk中託管的域名隱藏簽發萬用字元Let’s Encrypt 的功能。
為了防止客戶嘗試簽發萬用字元Let’s Encrypt 證書失敗,請如下操作:
-
轉到 擴展 > 「我的擴展」標籤 > 點按 SSL It! 旁的 打開。
-
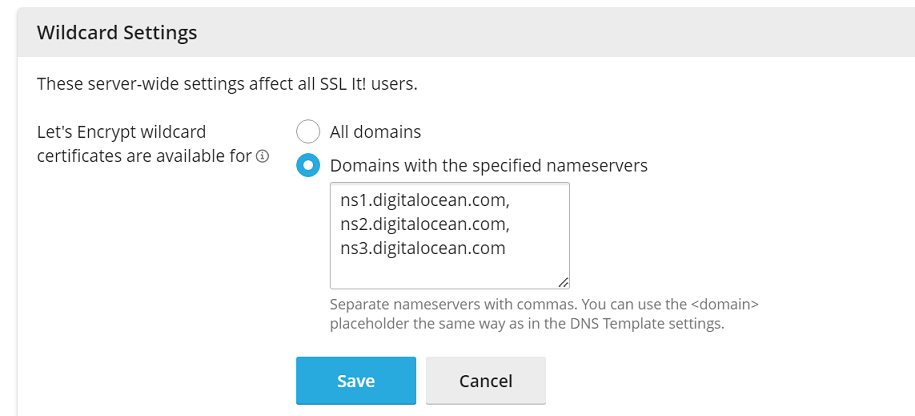
在螢幕的頂部,點按“設定”,然後選擇“具有指定域名伺服器的域名”。
-
在下面的文字方塊中,指定其DNS記錄在Plesk中託管的域名或與Plesk同步的協力廠商DNS服務(DigitalOcean DNS、Amazon Route 53 或 Azure DNS)中的域名伺服器。
用逗號分隔不同的域名伺服器。要指定其DNS記錄在Plesk中託管的所有域名的域名伺服器,您可以使用
<domain>預留位置:ns1.<domain>, ns2.<domain>
-
按一下 保存 。
客戶現在只能為可以自動保護安全的域名簽發萬用字元 Let’s Encrypt 證書。
您還可以通過 CLI 隱藏簽發萬用字元Let’s Encrypt證書的功能。為此,請運行以下模式的命令:
plesk ext sslit --wildcard-configuration -enable –nameservers 'ns1.<domain>,ns2.<domain>'
若要查看更多詳情,請運行 plesk ext sslit --help 命令。
限制訂購付費 SSL/TLS 證書的功能
這可能會限制客戶從某些供應商訂購付費 SSL/TLS 證書的功能,或會隱藏“獲取證書”按鈕。客戶仍然可以使用 Let’s Encrypt 的 SSL/TLS 證書來保護其網站的安全。
限制從一個或多個供應商訂購付費 SSL/TLS 證書的功能:
-
在 「[extensions]」 下,添加以下行:
blacklist = <comma-separated list of IDs of SSL It! plugin extensions>
例如,若要限制從 Symantec (DigiCert) 訂購SSL/TLS證書的功能,請添加以下幾行:
[extensions] blacklist = symantec
限制從某個供應商訂購付費的SSL/TLS證書的功能,將不會影響到已經從該供應商購買了SSL/TLS證書的客戶。要恢復從供應商處訂購付費 SSL/TLS 證書的功能,請通過再次編輯panel.ini文件從黑名單移除相應 SSL It! 外掛程式擴展的 ID。
隱藏 「獲取證書」 按鈕:
-
在
[ext-sslit]下,添加以下行:showGetMoreCertificatesLink = false
隱藏“獲取證書”按鈕將不會影響已經購買了SSL/TLS證書的客戶,也不會影響客戶使用Let’s Encrypt 的 SSL/TLS證書保護其網站安全的功能。此外,如果在伺服器上安裝了Sectigo擴展,客戶將能夠從Sectigo訂購付費證書,儘管“獲取證書”按鈕已被隱藏。要使按鈕可見,請通過再次編輯panel.ini文件來移除該行。